Strong wallet security is becoming more and more necessary as cryptocurrency adoption rises. Whether you are a full-time cryptocurrency trader or a part-time investor, safeguarding your digital assets ought to be your first concern. Knowing the difference between hot and cold wallets—and how to secure them—is crucial, as phishing, hacking, and user carelessness have cost billions of dollars.
In this blog, we’ll explore what crypto wallets are, the pros and cons of hot vs cold wallets, and practical security tips to help you safeguard your holdings. We’ll also touch on how tools like temporary email services—such as mytemp-mail and 10minutesmails—can further enhance your crypto privacy and safety.
What Is a Crypto Wallet?
A crypto wallet is a piece of hardware or software that lets users manage and keep track of their private and public keys for cryptocurrencies. Crypto wallets, as opposed to physical wallets, protect the cryptographic credentials that provide access to blockchain-based assets rather than the actual coins.
There are two primary types:
-
Hot Wallets – Connected to the internet
-
Cold Wallets – Offline and disconnected from the internet
Let’s break these down.
What Is a Hot Wallet?
A hot wallet is any crypto wallet that remains connected to the internet. These are typically used for daily transactions and active trading.
🔥 Examples of Hot Wallets:
-
Software wallets (e.g., MetaMask, Trust Wallet, Exodus)
-
Web wallets (e.g., exchange-based wallets like Binance or Coinbase)
-
Mobile wallets (app-based)
✅ Advantages:
-
Quick and easy to use
-
Ideal for frequent transactions
-
User-friendly interfaces
-
Often free
❌ Disadvantages:
-
More vulnerable to hacks, phishing, and malware
-
Prone to third-party breaches if stored on an exchange
-
Internet exposure increases security risk
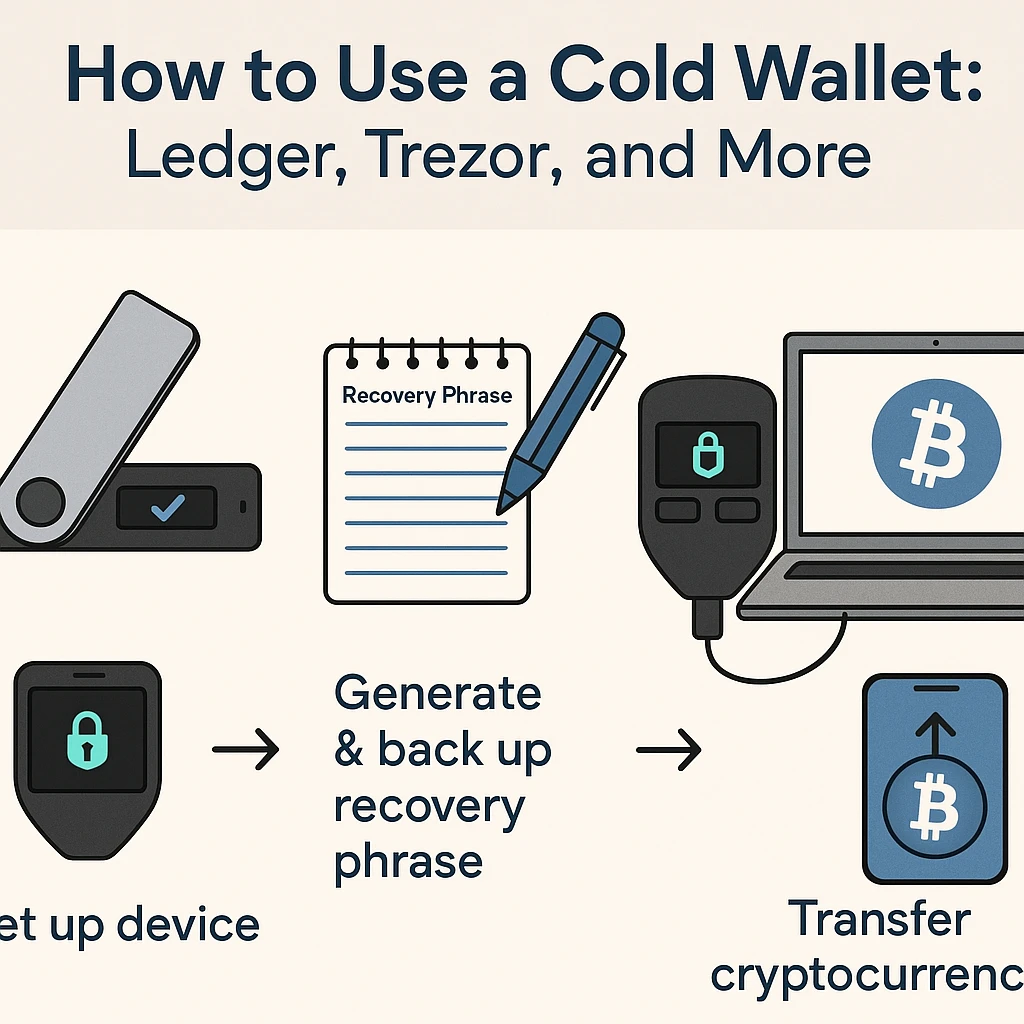
What Is a Cold Wallet?
A cold wallet is a wallet that is not connected to the internet, offering a more secure method of storing crypto assets for the long term.
❄️ Examples of Cold Wallets:
-
Hardware wallets (e.g., Ledger Nano S/X, Trezor)
-
Paper wallets (printed private/public keys)
-
Air-gapped computers with secure wallets
✅ Advantages:
-
Immune to online attacks
-
Best for long-term holding (HODLing)
-
Offers greater control and peace of mind
❌ Disadvantages:
-
Not suitable for everyday transactions
-
Can be lost or damaged if not backed up properly
-
Hardware wallets cost money (typically $50–$200)
Crypto Wallet Security Tips
These suggestions will help you improve security and stop unwanted access to your digital assets, regardless of the wallet type you use.
1. Use a Strong and Unique Password
A surprising number of wallet breaches occur due to weak or reused passwords.
✅ Use a password manager to generate and store complex passwords
✅ Avoid using personal information (birthdays, pet names, etc.)
✅ Never reuse passwords across platforms
2. Enable Two-Factor Authentication (2FA)
Always turn on 2FA for wallets, exchanges, and email accounts linked to your crypto activity.
-
Use an app like Google Authenticator or Authy
-
Avoid SMS-based 2FA when possible (vulnerable to SIM swapping)
3. Use Temporary Emails for Risky Platforms
When signing up for airdrops, DeFi apps, or untested crypto platforms, avoid exposing your primary email address. Instead, use services like:
Benefits:
-
Avoid spam and phishing
-
Minimize tracking and profiling
-
Safeguard your main accounts
4. Avoid Storing Crypto on Exchanges
Exchanges are tempting targets for hackers. Millions have been lost in high-profile exchange hacks (Mt. Gox, FTX, KuCoin, etc.).
✅ Always withdraw crypto to a private wallet you control
✅ Treat exchanges like ATMs—good for transactions, not storage
5. Backup Your Seed Phrase Properly
Your seed phrase (aka recovery phrase) is the key to your crypto wallet. If lost, your funds are gone forever.
✅ Write it down on paper (never store digitally)
✅ Keep multiple copies in safe locations
✅ Consider using a fireproof safe or steel backup (e.g., Cryptosteel)
6. Stay Updated on Wallet Software and Firmware
Update your hardware wallet's firmware and wallet apps on a regular basis. Security flaws are fixed and enhancements are made with these updates.
7. Use a Dedicated Device for Crypto Activity
For higher security:
-
Use a separate phone or computer for accessing wallets
-
Avoid installing unrelated apps or browsing non-crypto websites on that device
This minimizes the risk of malware infections or phishing.
8. Watch for Phishing Scams
Scammers often impersonate wallet providers, exchanges, or airdrop sites to steal your keys.
⚠️ Never click on suspicious links in emails or DMs
⚠️ Bookmark official sites and double-check URLs
⚠️ Be cautious of fake customer support channels on social media
9. Secure Your Internet Connection
Public Wi-Fi is not safe for crypto transactions. Always use:
-
A secure, private network
-
A trusted VPN to encrypt your data
10. Don’t Share Screenshots or QR Codes Publicly
Displaying your wallet address, QR code, or even screenshots of your interface may expose you to social engineering, dusting attacks, or targeted scams.
Additional Tip: Multisig Wallets for Shared Funds
Gnosis Safe and other multisig wallets are good options for teams or DAOs handling cryptocurrency funds. By requiring several private keys to approve a transaction, these wallets lessen the possibility of a single point of failure.
The Role of Temp Mail in Crypto Privacy
Temporary email services like mytemp-mail and 10minutesmails are becoming essential tools for crypto users.
Use temp mails when:
-
Signing up for airdrops
-
Testing Web3 dApps
-
Avoiding newsletter spam
-
Creating throwaway crypto accounts
They provide an added layer of anonymity and prevent email-targeted phishing.
Final Thoughts
The security of your wallet is an unavoidable obligation, regardless of how much money you have in crypto or how big your portfolio is. Knowing how hot and cold wallets operate and how to use each effectively is essential given the range of threats, from phishing scams to full-fledged hacks.
Here's a quick recap:
-
Use hot wallets for convenience, cold wallets for long-term security
-
Always back up your seed phrase and never share it
-
Enable 2FA and use password managers
-
Avoid storing funds on exchanges
-
Use mytemp-mail and 10minutesmails for privacy protection during signups
In crypto, you are your own bank—so take that responsibility seriously. A few smart habits today can protect your future wealth for years to come.



Leave a Reply